A Directed Acyclic Graph (DAG) is a data structure that connects points with one-way links and never loops back.
What is a directed acyclic graph (DAG)?
A Directed Acyclic Graph (DAG) is a data structure that organizes information in a graph format where edges have a defined direction, and no cycles exist. It means that once a transaction or piece of data is added, it cannot be altered or reverted. Due to their efficiency in structuring and verifying information, DAGs are widely used in various fields, including cryptography, machine learning, and data processing.
In the context of cryptocurrencies and distributed ledger technology, DAGs provide an alternative to traditional blockchain structures. DAGs arrange transactions in a web-like format. Each new transaction must reference and verify previous transactions, creating a decentralized yet highly efficient validation system.
This innovative structure allows DAGs to process transactions faster and with lower fees, making DAG-based solutions an appealing choice for crypto payments.
How transactions are processed in a DAG-based system
DAG-based systems operate differently from blockchain. DAGs process transactions asynchronously. Each new transaction verifies one or more previous transactions before being added to the network. It eliminates the need for blocks and miners, making the system more efficient and scalable. The more transactions a DAG processes, the more secure and decentralized it becomes.
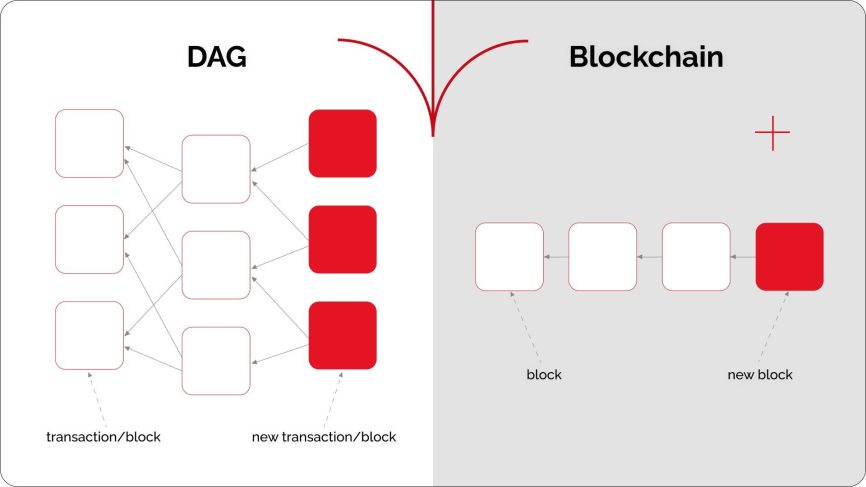
Differences between DAG and traditional blockchain
DAGs and blockchains serve as distributed ledgers, but their architectures differ significantly.
Here are the key differences:
- Structure:
Blockchain networks form a sequential chain of blocks, each containing a batch of transactions. DAGs, on the other hand, form a network of interconnected transactions without fixed blocks. - Fees:
Miners or validators secure blockchain transactions and receive rewards, leading to transaction fees. In DAG-based systems, fees are typically lower or nonexistent since users participate in validation themselves. - Transaction speed:
Blockchains process transactions one block at a time, often requiring waiting periods for confirmation. DAGs allow simultaneous transaction processing, leading to near-instant confirmations. - Scalability:
Blockchains struggle with scalability due to limited block sizes and network congestion. DAGs, by design, become faster and more efficient as transaction volume increases. - Energy consumption:
Traditional blockchains, especially those using Proof of Work (PoW), utilize significant energy. DAGs eliminate mining, which reduces energy consumption and makes them a greener alternative.
These distinctions make DAGs an attractive option for businesses seeking fast, cost-effective, and scalable distributed ledger solutions.
What are the examples of DAG-based cryptocurrencies?
Several projects have adopted DAG technology to improve transaction efficiency and scalability. Here are some prominent examples:
- Fantom (FTM): Fantom employs a DAG-based consensus protocol called Lachesis, which enables fast and secure transactions while supporting smart contracts. It aims to provide a more scalable alternative to Ethereum, catering to decentralized applications (dApps).
- IOTA (MIOTA): It’s a DAG-based cryptocurrency designed for the Internet of Things (IoT). Because of its Tangle structure, each transaction validates two previous ones, ensuring lower transaction fees and scalability. It makes IOTA ideal for machine-to-machine microtransactions.
- OByte (GNYTE): OByte combines a DAG cryptocurrency with a decentralized database for payments and smart contracts. Its structure ensures secure execution and has been applied in healthcare for tracking patient data with integrity and accessibility.
- Nano (XNO): Unlike most cryptocurrencies, Nano uses a block-lattice structure – an enhanced form of DAG. Each account has its own blockchain, allowing for instant, zero-fee transactions. Nano’s efficiency makes it a strong contender for everyday digital payments.
- Hedera Hashgraph (HBAR): Hedera uses a DAG-based structure Hashgraph for fast, fair, and secure transactions. Hedera’s gossip-about-gossip protocol and virtual voting enable high-speed consensus, making it ideal for supply chain tracking and transparency.
These projects demonstrate DAG’s potential to revolutionize digital payments and decentralized networks.
Advantages of DAG technology
DAG technology offers multiple advantages over traditional blockchains, which makes it an attractive choice for businesses and developers. Key benefits include:
- Higher transaction throughput:
DAGs support parallel transaction processing and therefore allow thousands of transactions per second without congestion. - No mining required:
Without miners, DAG networks eliminate costly mining operations, which reduces overall transaction costs. - Zero or minimal fees:
Users validate transactions themselves, removing the need for fees paid to miners or validators. - Improved scalability:
Unlike blockchains that experience slowdowns with increased usage, DAGs become more efficient as network activity grows. - Energy efficiency:
Without PoW mining, DAG networks consume far less energy. Thus, this technology is rather eco-friendly. - Suitable for micropayments:
The absence of fees and high-speed transactions make DAGs suitable for microtransactions, such as IoT payments and digital tipping.
Challenges and limitations of DAG
Despite its potential, DAG technology faces several challenges:
- Security concerns: DAG networks rely on a high volume of transactions for security. Low transaction activity can make them vulnerable to attacks.
- Decentralization issues: Some DAG implementations require centralized coordinators during early development stages, raising concerns about network control.
- Limited adoption: While promising, DAGs are still in their early stages compared to blockchain technology, making widespread adoption a challenge.
- Lack of standardization: Most DAG-based networks use unique consensus mechanisms and thus complicate interoperability between different platforms.
- Sybil attacks: Without proper protections, malicious actors can generate numerous fake identities to manipulate DAG-based networks.
Despite these limitations, ongoing research and development are addressing these concerns, paving the way for broader adoption in the future.